4c Security XDR Platform
4C Security XDR Platform Unified, Adaptive, Intelligent
At the core of our cybersecurity strategy lies the 4C Security XDR Platform — an integrated, intelligent defense system that brings together every layer of protection into one seamless architecture.
The visual below represents the modular architecture of the 4C XDR Platform — unifying collection, analysis, correlation, and automated security workflows into one intelligent ecosystem.
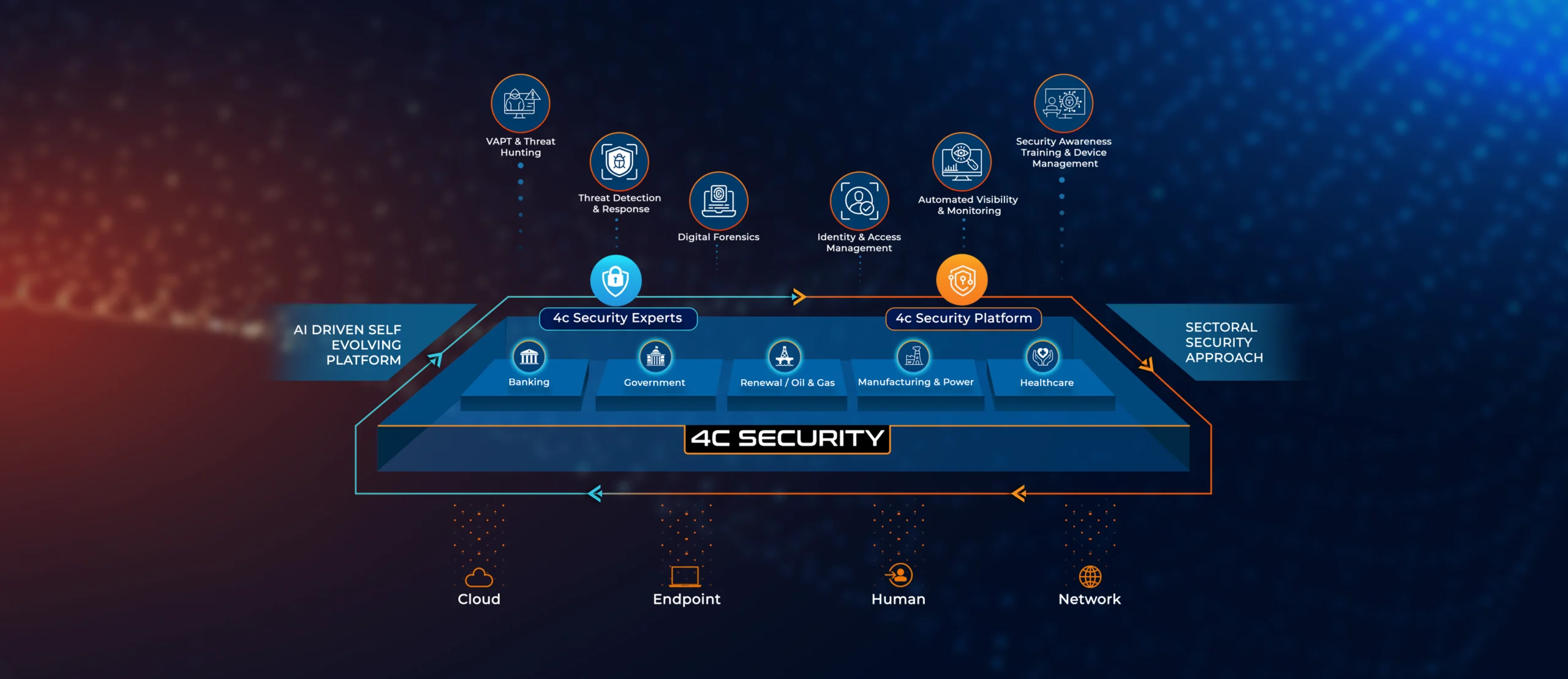
Key Layers of the Architecture:
VAPT & Threat Hunting
Continuously scans for vulnerabilities and IoCs to identify threats early and strengthen defenses.
Threat Detection & Response
Real-time threat monitoring with intelligent response playbooks that adapt based on the nature and scope of the threat.
Digital Forensics
Detailed incident investigation tools to analyze attack vectors, recover lost data, and ensure compliance during audits.
Identity & Access Management (IAM)
Advanced user authentication, privilege management, and behavioral analytics to minimize insider risk and unauthorized access.
Automated Visibility & Monitoring
Always-on monitoring across hybrid environments with real-time insights and AI-driven anomaly detection.
Security Awareness Training & Device Management
Bridges the human gap by training users, enforcing secure device usage, and reducing the chances of phishing, ransomware, or credential theft.
A Platform That Grows With You
Your threat landscape won’t be the same six months from now — and neither should your defense strategy.
Scalable integrations
Scalable integrations with third-party tools, platforms, and services.
AI-driven threat modellin
AI-driven threat modelling that evolves over time
Self-healing capabilities
Self-healing capabilities that reduce manual intervention
Customizable dashboards
Customizable dashboards for CISOs, SOC analysts, and IT teams.
Built for the Hybrid Enterprise
See the Platform in Action
Curious how it fits your environment? Let’s show, not just tell.
Our team will walk you through real-world scenarios, map it to your current infrastructure, and help you unlock the next level of cyber resilience.
